Part 4 of “Baked in and Wired: eDiplomacy @ State“
| « Read Part 3: Public Diplomacy | Read Part 5: Knowledge Management for eDiplomacy Resources » |
What’s the Issue?
Internet freedom was until recently not a foreign policy issue. Newton-Small traces the origins of the policy to a conversation four years ago:
In 2008, Michael Horowitz, a longtime religious-liberty advocate, went to his friend, Representative Frank Wolf, a Virginia Republican, and suggested setting aside funds to help Falun Gong, a religious group that Beijing has labeled a dangerous cult. The money was supposed to help the dissidents distribute software to jump China’s massive firewall and organize online as well as communicate freely with the outside world. Wolf succeeded in appropriating $15 million, but U.S. diplomats feared the move would derail relations with Beijing, and little money was spent.
The reality of how the issue actually percolated to the U.S. Congress is more complex, however; it was not until September 2009 that Secretary Clinton first used the term internet freedom in a speech, and then only in passing. It was in January 2010 in her Newseum speech, that Clinton sketched out what would become a mainstream U.S. foreign policy (the policy was later refined in a February 2011 speech).
Promoting and facilitating internet freedom is among the most radical uses ediplomacy is being put to at State. Its starting point is that America’s traditionally strong advocacy for civil liberties should apply fully and without exception to the online world. Thus, if a government seeks to restrict these freedoms online, the U.S. government will oppose it both rhetorically and in practice including by directly funding the development and rollout of tools that will subvert restrictive internet policies. The use of technology to overcome censorship and empower individuals in exercising their human rights online is a forward-leaning aspect of U.S. policy that views human rights online the same as it does in the physical world. The United States does not condone or seek to support illegal online activity (such as transnational crime) but leaves it to itself to be the arbiter of when and what type of monitoring and filtering is acceptable.
It is a policy that has been framed in epic proportions. In October 2011, Secretary Clinton’s Senior Adviser for Innovation Alec Ross was reported by the Washington Post as saying:
If the great struggles of the 20th century were between left and right, he said, the conflict of the 21st century will be between open and closed. ‘The president and the secretary of state have made it clear where they stand on this,’ he said. ‘For openness, with an open Internet at its core.’
Unsurprisingly, this is a hugely controversial foreign policy. It positions (p. 24) the United States in direct opposition to important emerging powers like China as well as other authoritarian states the United States more commonly treats as partners (such as Vietnam and Bahrain). The policy also implies a call on all democratic societies to join it in countering censorship and monitoring. However, even some very close allies such as Australia and the United Kingdom have, at times, pursued inimical policies – and even the United States has found it hard to live up to its own policy (see challenges below).
In many respects Congress and State were ahead of their time on this issue. The Arab uprisings, which began at the end of 2010, revealed the extent of monitoring in places like Libya (and the complicity of Western companies in providing surveillance equipment). It also raised awareness among many authoritarian governments about the power of connection technologies to facilitate revolt, fuelling further demand for monitoring and filtering technologies. As the Washington Post reported in a December 2011 article on a trade show for makers of surveillance equipment run by entrepreneur Jerry Lucas:
The most popular conference, with about 1,300 attendees, was in Dubai this year. Middle Eastern governments, for whom the Arab Spring was ‘a wake-up call,’ are the most avid buyers of surveillance software and equipment, Lucas said.
The rapid and sustained spread of the protests across the Arab world and beyond also appears to have fed into State’s thinking on internet freedom.
Clinton’s Newseum speech – delivered nearly a year to the day before President Ben Ali of Tunisia was ousted – was a shot across the bow, laying out the broad parameters U.S. policy would take. It framed the issue in terms of universal human rights, in particular freedom of expression and freedom of worship.
While some dismissed the speech as being overly optimistic, it was not without its caveats, noting the internet is a neutral technology that does ‘not take sides in the struggle for freedom and progress’ and acknowledging it could just as easily be used for good as ill.
By couching internet freedom in the language of rights, Clinton provided one rationale for direct U.S. government intervention to promote internet freedom in other countries. But the speech also offered another reason that equated restrictions on the internet with an attack on what Clinton called “the global networked commons.”
States, terrorists, and those who would act as their proxies must know that the United States will protect our networks. Those who disrupt the free flow of information in our society or any other pose a threat to our economy, our government, and our civil society. Countries or individuals that engage in cyber attacks should face consequences and international condemnation. In an internet-connected world, an attack on one nation’s networks can be an attack on all. And by reinforcing that message, we can create norms of behavior among states and encourage respect for the global networked commons.
The speech also laid out the approach the United States would take to implement this agenda: At a big-picture level, global political action; and at a technical level, support for the development of technologies “that enable citizens to exercise their rights of free expression by circumventing politically motivated censorship’ and training.”
It was envisaged activists would use these technologies across a very broad range of issues, with Clinton stating:
We want to put these tools in the hands of people who will use them to advance democracy and human rights, to fight climate change and epidemics, to build global support for President Obama’s goal of a world without nuclear weapons, to encourage sustainable economic development that lifts the people at the bottom up.
The follow-up speech shied away from this more optimistic vision and focused on what Clinton called “the challenges we must confront as we seek to protect and defend a free and open internet.” These were described as “achieving both liberty and security,” “protecting both transparency and confidentiality” and “protecting free expression while fostering tolerance and civility.”
The speech focused on the tensions and complexities of internet freedom and the fact they defy easy resolution and tidy divisions of the world into black and white, while also addressing the criticisms the policy had received since the Newseum speech. For example, how to square a free and open internet with U.S. policy that regards the theft of intellectual property, State Department cables or child pornography as crimes? (Clinton argued freedom on the internet is an extension of human freedom in the real world. Just as walking out the doors of the State Department with a briefcase full of printed diplomatic cables would be regarded as theft, so too was obtaining them electronically. In essence, what is illegal in the offline world should be illegal online too.)
The speech also included a defense of the approach the Department has taken with the development of circumvention technologies arguing in favor of “a venture capital-style approach, supporting a portfolio of technologies, tools, and training, and adapting as more users shift to mobile devices,” rather than a focus on a single technology.
The U.S. government’s establishment of internet freedom as a foreign policy priority has presented State with a hugely complex policy issue. It complicates important bilateral relations, it is a never-ending innovation battle pitting U.S.-funded circumvention technologies against the massive resources of countries like China dedicated to stifling freedom of speech and communication, and it is a policy very hard to live up to. Poorly executed, it also risks endangering activists. So how is State responding?
Internet Freedom at State
From 2008 to 2012, the State Department will have spent close to $100 million on internet freedom related activities. The grants are used to fund a range of activities. As the Department put it in its May 2012 grant solicitations (a detailed official version is available here):
Since 2008, State and USAID have invested $76 million in efforts to advance human rights online. Through this call we intend to support at least $23 million in additional programs in the following areas: 1) anti-censorship technology, 2) secure communications technology, 3) digital safety training, 4) emergency response support for netizens and civil society organizations under threat, 5) policy and advocacy, 6) research and evaluation on the technology and political context for Internet repression, and 7) research on technology options for expanding the free flow of information in extremely constrained environments.
The bulk of this funding has been spent on the first three areas. The funding categories also suggest that notwithstanding Secretary Clinton’s claim the policy included efforts “to fight climate change and epidemics, to build global support for President Obama’s goal of a world without nuclear weapons,” the focus of State’s internet freedom funding is on helping activists in extremely repressive societies and presumably those focussed on human rights and democracy promotion.
State uses the funding rounds to outsource the development of these tools to third parties—usually NGOs. The bulk of funding is channelled through the Bureau of Democracy, Human Rights and Labor (DRL). However, the Bureau of Near Eastern Affairs’ Iran desk and the Iran program are also involved in Iran focussed campaigns (that draw on DRL expertise).
Many of the projects State funds have not been made public due to the sensitive nature of this work, but some have. The first paper in this series provides some details (pp. 23-25). Three of these include:
- The Commotion Project (sometimes referred to as the “Internet in a Suitcase”). This is an initiative from the New America Foundation’s Open Technology Initiative to build a mobile mesh network that can literally be carried around in a suitcase, to allow activists to continue to communicate even when a government tries to shut down the Internet, as happened in several Arab Spring countries during the recent uprisings.
- The Panic Button, “InTheClear.” This is being developed by Mobile Active and is currently in Beta release. The application allows activists to instantly erase all the contacts and messages on their phone if they are arrested. It also lets them send a message to their contacts warning them that they have been arrested.
- A circumvention campaign. This was run by InterNews, a global NGO working on the promotion of local media. One recent circumvention campaign it developed and rolled out operated in 12 authoritarian countries: Bahrain, Burma, China, Egypt, Ethiopia, Iran, Syria, Tunisia, Turkmenistan, Uzbekistan, Vietnam and Yemen. The campaign lasted for between six to 12 months in each country and ran advertisements on Google, Facebook and local social media platforms as well as local banner campaigns on popular websites (see examples below). So, for example, if a user were searching for a blocked site on Google, instead of just getting a government message that the site was blocked or unavailable, they would also get a Google ad offering them the opportunity to get around the government firewall.



The fact much of its internet freedom activities remain unreported makes assessing their impact almost impossible. RAND has been awarded a State Department grant to conduct a comprehensive review, but this has yet to be finalized.
Even without a detailed picture of State’s successes or failings in this new policy space, it is possible to identify several challenges it must confront.
Challenges
Despite the various attempts to explain and promote a coherent internet freedom policy, several tensions and contradictions trouble it.
In her Newseum speech, Secretary Clinton said, “Countries or individuals that engage in cyber attacks should face consequences and international condemnation.” Yet earlier this year, it was revealed that the United States had itself been involved in directing cyber attacks against Iran since 2006. As David Sanger reported it in the New York Times:
Mr. Obama, according to participants in the many Situation Room meetings on Olympic Games, was acutely aware that with every attack he was pushing the United States into new territory, much as his predecessors had with the first use of atomic weapons in the 1940s, of intercontinental missiles in the 1950s and of drones in the past decade. He repeatedly expressed concerns that any American acknowledgment that it was using cyber weapons—even under the most careful and limited circumstances—could enable other countries, terrorists or hackers to justify their own attacks.
Although these sorts of cyber attacks on Iran’s nuclear facilities are distinguishable from attacks on free speech there is a difficult tension in U.S. policy here. Cyber attack-like methods are often used to stifle free speech. And use of even limited cyber attacks clearly undermines the United States’ broader effort to create an international norm against the use of such attacks. This approach is doubly problematic given the barriers to entry for cyber attacks are significantly lower than those required to develop atomic and other weapons.
To an extent, the U.S. is, for the most part, going to be able to ride this controversy out. U.S. cyber attacks were not directed at Iranians trying to access the internet, but rather computers used in Iran’s nuclear facilities. And because U.S. policy towards Iran is openly hostile and focused on regime change it will come as a surprise to no one that the United States is doing whatever it can to undermine the Iranian regime and stop its acquisition of nuclear weapons. Notwithstanding this, when China, Russia or other countries carry out similar attacks, U.S. rhetoric on internet freedom will carry less weight.
Another challenge is dealing with close partners and allies who undermine internet freedom. In August 2011, in the midst of the Arab uprisings, the UK experienced a different connection technology infused movement, the London Riots. On August 11, in the heat of the crisis, Prime Minister Cameron told the House of Commons:
Free flow of information can be used for good. But it can also be used for ill. So we are working with the police, the intelligence services and industry to look at whether it would be right to stop people communicating via these websites and services when we know they are plotting violence, disorder and criminality.
This policy had far-reaching implications. As recently as January 2011, then President of Egypt, Hosni Mubarak, ordered the shut-down of Egypt’s largest ISPs and the cell phone network, a move the United States had heavily criticized. Now the UK was contemplating the same move and threatening to create a rationale for authoritarian governments everywhere to shut down communications networks when they threatened “violence, disorder and criminality.”
Other allies like Australia are also pursuing restrictive internet policies. As OpenNet reported it:
“Australia maintains some of the most restrictive Internet policies of any Western country…”
When these allies pursue policies so clearly at odds with the U.S. internet freedom agenda, several difficulties arise. It undermines the U.S. position that an open and free internet is something free societies naturally want. It also gives repressive authoritarian governments an excuse for their own monitoring and filtering activities. To an extent, U.S. internet freedom policy responds even-handedly to this challenge because the vast bulk of its grants are for open source circumvention tools that can be just as readily used by someone in London as Beijing, but so far, the United States has been much more discreet about criticising the restrictive policies of allies than authoritarian states.
A further contradiction with the policy is that U.S. companies are contributing towards the restrictive internet environment that its internet freedom policy is trying to overcome. The Washington Post carried a detailed report in December 2011 of what has become known as the “Wiretappers’ Ball.” The event the Post reported on in Maryland brought together representatives from 43 countries to buy serious surveillance packages including from 15 U.S.-based corporations (as well as many foreign ones). As the Post described it:
On offer were products that allow users to track hundreds of cellphones at once, read e-mails by the tens of thousands, even get a computer to snap a picture of its owner and send the image to police—or anyone else who buys the software. One product uses phony updates for iTunes and other popular programs to infiltrate personal computers.
The article went on to report the entrepreneur behind the event:
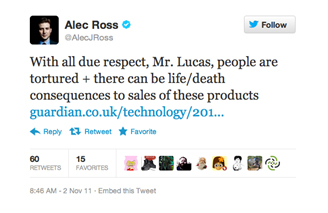
‘When you’re selling to a government, you lose control of what the government is going to do with it,” Lucas said. “It’s like selling guns to people. Some are going to defend themselves. Some are going to commit crimes.’
Lucas’ blasé attitude did not escape criticism with Alec Ross calling him out on Twitter.
In April 2012, the Obama Administration also responded with an Executive Order that, among other things, “blocks the property and interests of any individual or entity designated by the Secretary of Treasury to have…sold, leased, or otherwise provided any good, service, or technology to Iran or Syria, whether directly or indirectly, to facilitate network surveillance for human rights abuses by or on behalf of the Iranian or Syrian government.” As one law firm noted, “Given the priority assigned to the issue by the Administration and Congress, affected companies should anticipate additional laws in the United States that may further restrict their business.”
Critics of State’s internet freedom policy, such as Morozov in “The Net Delusion,” correctly point out that by entering into the fray, State risks inadvertently doing harm by, for example, developing circumvention tools that provide activists with a false sense of security. But that criticism is also too simplistic in a world where activists will continue organizing online whether or not State sponsors tools to help protect them – cell phones and the internet simply offer too great an advantage in terms of convenience, reach and speed.
Internet freedom is a long haul policy, and the resources Congress is allocating towards it are no match for those China, Russia and others are allocating to counter its advances. Still there is a lot of valuable work State can do in this space. Working to stop Western exports of surveillance equipment to human rights abusing regimes is one area in the traditional diplomatic space. It also makes sense to continue to fund the development of circumvention tools that will mitigate potential risks to activists. Certainly, there needs to be serious restraints on overoptimistic claims being made about these technologies and great care being taken when training activists. However, as the Arab uprisings continue to demonstrate, even when activists know their governments have highly sophisticated monitoring tools, they nevertheless continue to use them.
| « Read Part 3: Public Diplomacy | Read Part 5: Knowledge Management for eDiplomacy Resources » |
The Brookings Institution is committed to quality, independence, and impact.
We are supported by a diverse array of funders. In line with our values and policies, each Brookings publication represents the sole views of its author(s).